Hospital data breaches are emerging at an alarming rate and show no signs of slowing down in 2019. That’s because data fetches a hefty price on the black market, making hospitals prime targets for cybercriminals. The best way to defend against these threats is to arm your team with the following systems and protocols.
Why are hackers targeting healthcare?

For the past decade, the healthcare sector has been using digital records to effectively treat, track, and bill patients. Organizations such as hospitals, labs, pharmacies, drug companies, insurance providers, and outpatient clinics store massive amounts of protected health information (PHI) and personally identifiable information (PII) to improve accessibility and patient care.
Healthcare IoT: Security risks involved

The rule of cybersecurity states that anything that connects to the internet can be hacked. With the increasing popularity of Internet of Things (IoT) in the healthcare industry, every business should be on alert.
Devices that contain a treasure trove of patient data are attractive targets for cybercriminals.
How blockchain can revolutionize healthcare
4 Items in Your HIPAA Compliance Checklist

HIPAA’s rules pertaining to IT are problematic to say the least, but things have become much clearer over the course of the past year. However, there are still a few areas in which your office might not be compliant. This isn’t necessarily through negligence on your part, but rather a lack of understanding as to the requirements.
AI and its effects on healthcare
EHR hardware: you need to know
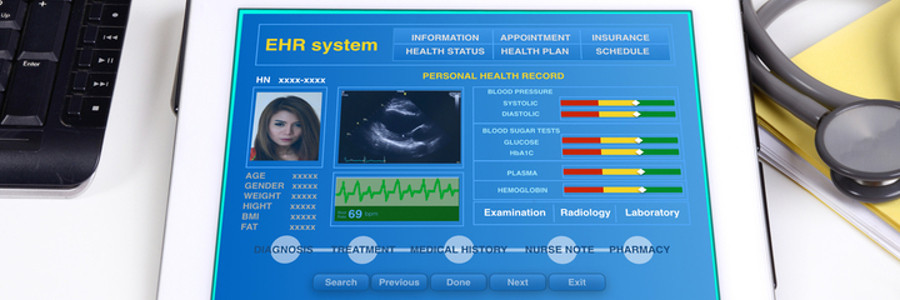
Medical history, vaccine status, lab test results, and other medical records are libraries unto themselves. Checking such files without the aid of computers can be cumbersome. Thanks to EHR, hospital staff can access these information with ease.
EHR stands for “Electronic Health Record,” and a lot can go into getting your practice ready for one of these data-sharing, network-connected, enterprise-wide information systems.
Features of Mobile Device Management in Healthcare

Surveys and studies show that wireless device usage in the healthcare industry is growing at an exponential rate, falling in line with the general trend in today’s society. The IT staff must work harder to monitor all the devices using the network, but there are Mobile Device Management (MDM) solutions that can make their jobs easier.
Mitigating healthcare insider threats

First off, what is an insider threat in healthcare? An insider threat is an individual inside an organization discovered to have been accessing healthcare records without authorization. Healthcare companies must take steps to reduce the potential for insider threats, which is their top source of security incidents.





