Mobile devices have become indispensable tools for employees, offering the flexibility to work from anywhere. However, with this convenience comes challenges, especially in terms of security. As cybercriminals target mobile devices with more sophisticated tactics, robust mobile security should be a nonnegotiable for businesses.
Blog
Essential tips and fixes when Windows won’t boot
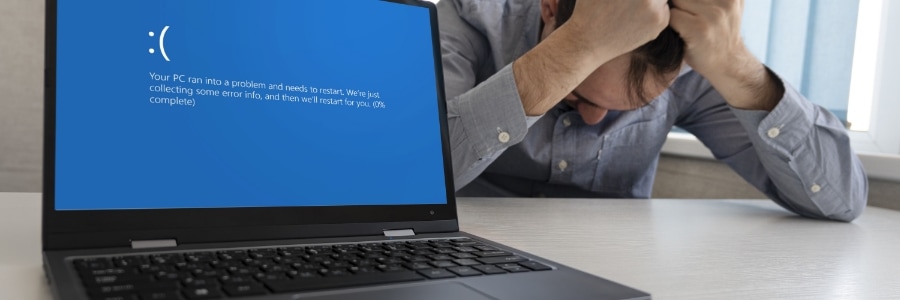
When your Windows PC fails to boot, it's essential to understand the potential causes and how to address them effectively. Boot issues can be caused by corrupted system files, hardware failures, or problematic software updates. Fortunately, there are several troubleshooting methods you can use to pinpoint the root cause and fix the issue.
Navigating your business to the cloud: A 5-step UC migration guide

Migrating your unified communications (UC) system to the cloud is a strategic move that promises enhanced security, scalability, and flexibility. However, it’s a complex journey that requires careful planning and execution. This guide outlines five essential steps to ensure a smooth and successful cloud migration for your business.
3 Security advantages of the cloud
Safeguard your company’s data with the right security measures

For a business leader like yourself, safeguarding your organization's data is a top priority. Data breaches can erode customer trust, damage your reputation, and ultimately affect your bottom line. Taking a proactive approach to data security demonstrates your commitment to protecting valuable information and fostering a culture of security awareness within your organization.
Lost or stolen device? You should have a mobile device incident response plan
Factors to consider when looking for the right small-business VoIP solution

Communication underpins any successful business, and Voice over Internet Protocol (VoIP) systems have redefined how companies address their communication needs. For small businesses, selecting the right VoIP system can bring about significant cost reductions, improved adaptability, and better scalability.







