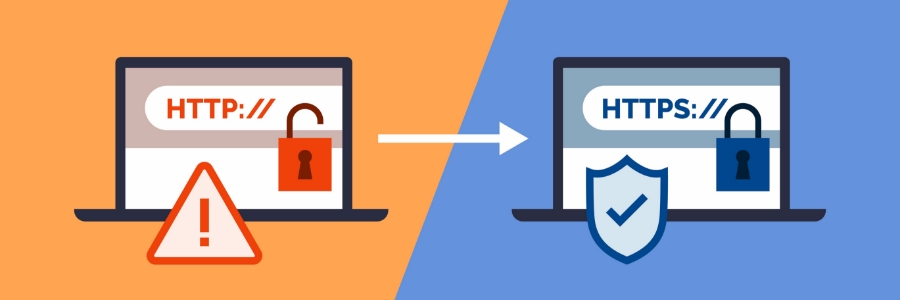
If you've never thought about how safe your information is while browsing the web, then it's time to start thinking about it. One of the best ways to ensure your safety is by visiting sites that use HTTPS, a protocol that helps keep your data secure when you're online.
The S in HTTPS: What it is and why you should care
A guide to IT security terms everyone should know

You've probably heard the term "malware" thrown around a lot, but what does it actually mean? In this article, we will define malware and a few other commonly used terms in IT so you can better protect your business. Understanding these basic cybersecurity concepts doesn’t require deep IT expertise, so read on.
Safeguard your Android devices from ransomware

Ransomware is a type of malware that locks users out of their devices or encrypts their data until a ransom is paid. This form of attack has become increasingly widespread in recent years, and it has even begun to target Android devices. This certainly poses a threat to any business, so it's important that you learn how ransomware affects Android devices and how you can protect against this cyberthreat.
What is a password spraying attack, and how can you protect your business from one?

The most common way passwords are compromised is through brute force attacks. This is where cybercriminals attempt to infiltrate an account by guessing both common and random password combinations. However, more and more cybercriminals are now using password spraying to gain access to their victims' accounts.
Securing Microsoft Teams: Practical tips to keep your workplace safe

Microsoft Teams is a great tool that can help improve communication and collaboration in the workplace. However, the popular business communication platform can also be a security concern if it's not adequately secured. In this blog, we’ll dive into some practical tips for securing Microsoft Teams and keeping your workplace safe.
Protecting your Microsoft 365 environment and data

For many businesses, Microsoft 365 is their go-to productivity suite because it offers powerful features, cost-saving benefits, and world-class security. And while Microsoft continuously looks for ways to address security concerns, the changing threat landscape can put Microsoft 365's security measures to the test.
The three kinds of hackers every business should watch out for

Hackers come from all different backgrounds. Some hackers are motivated by money and politics, while others simply hack systems for fun. In this blog post, we will define the three kinds of hackers and how each one differs from the others.
A complicated history
In the 1950s, the term “hacker” was vaguely defined as someone who explored the details and limits of computer technology by testing them for a variety of purposes.
4 Alarming cybersecurity statistics this 2022 and what they mean for your organization

As cyberthreats become more dangerous and prevalent, cybersecurity should become a top priority for businesses of all sizes. Despite this, many organizations still don't take the proper steps to protect their data and systems. To help you understand just how important cybersecurity is, we collected four statistics you need to know:
1. Small businesses experience more attacks than big businesses
Between January 2021 and December 2021, researchers at IT security company Barracuda Networks analyzed millions of emails across thousands of organizations.