The Health Insurance Portability and Accountability Act (HIPAA) requires organizations to ensure the confidentiality, integrity, and availability of protected health information (PHI). Companies that fail to comply often meet steep penalties that cost hundreds of thousands of dollars. This is not exclusive to healthcare-related firms, either. Any company that manages PHI (your employees’ data may have their PHI for medical insurance) must be HIPAA compliant.
Health data is highly sought after by cybercriminals. Malware and data breaches can cause major service disruption and other disastrous consequences. So, if your organization is governed by HIPAA regulations, you need to follow these data security tips.
Test your security
HIPAA requires members to conduct risk assessments that include reviewing security policies and systems for vulnerabilities. Frequently evaluating your system’s security is the best way to make sure there are no gaps left for attackers to exploit and get their hands on health records.
HIPAA also requires members to conduct risk assessments that include reviewing security policies and systems for vulnerabilities. Security specialists can conduct regular vulnerability assessments to identify the weaknesses in your network. It's also a good idea to perform penetration tests. This method of security testing simulates a malicious attack or data breach on your information systems. Results can be analyzed to better improve security and reliability and ensure compliance.
Establish a culture of security
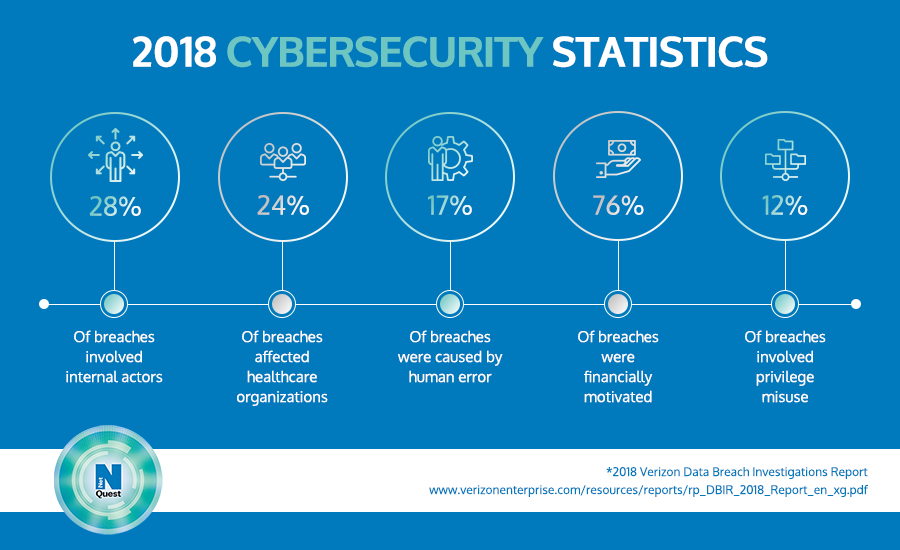
A report by Verizon showed that human errors were the cause of one in five data breaches in 2018, proving what IT professionals have always known: employees are the weakest link in security.
One way to mitigate this is by establishing a culture of strict adherence to HIPAA rules and regulations. This includes training in carefully following security protocols such as setting strong passwords, enabling multifactor authentication, and an awareness of red flags, threats, and risks that include more than unsolicited emails and strange websites.
As compliance standards, risks, threats, and tactics change and evolve over time, employees should be continually educated of the impact of these changes on day-to-day tasks and should be made thoroughly aware of the implications of violations and data breaches.
Be vigilant with devices
Any HIPAA-covered entity must implement a number of security controls on devices that access, store, and transmit PHI. Solutions to these vulnerabilities will likely include access controls, firewalls, anti-malware programs, and user authentication up to more advanced ones like mobile device management.
Hold business associates accountable
Healthcare organizations often have to deal with a diverse set of partners such as vendors, insurance companies, and labs. Ensure that all business associates who have access to your patient data agree to follow HIPAA standards and protocols with legally binding agreements.
Agreements should hold business associates accountable for providing security measures and risk assessments that safeguard your patient data. As a HIPAA-covered entity, your organization is ultimately responsible for security and privacy violations.
Encrypt and reassess
Encrypt all PHI data to avoid any privacy breaches. This includes encrypting PHI data as it's being transmitted over the internet. Even though a loss of encrypted data is not considered a breach by HIPAA, it is required under HIPAA to reassess requirements for encryption yearly. This is all part of the continuous process of reviewing and improving your system protections.
Upgrade your email security
The email of healthcare professionals is often the target for phishing and ransomware. It pays to upgrade to an advanced email filtering solution specifically designed for HIPAA compliance. These have more sophisticated security mechanisms designed to defend against the latest email-based threats targeting healthcare.
Secure your network
An essential technique for restricting network access is to set up separate networks: one should be dedicated to guest activity and another should be built for medical devices and applications that transmit and carry ePHI.
What’s more, you need the advanced network security stance of a SOC 1 and SOC 2 audited data center from a HIPAA hosting company. Advanced network security such as this will be able to detect and mitigate any risk to your PHI data.
Consult or partner with a security expert that will allow your organization to keep focusing on patient care, while it does the tedious task of defending your network and databases. Contact Netquest today.
Like This Article?
Sign up below and once a month we'll send you a roundup of our most popular posts